DoS & DDoS ATTACK….

Introduction to Dos attack :-
Dos attack(Denial-of-Service) is a cyber attack in which attacker send lots of requests(traffic) simultaneously at a time to the target server or network, due to which it become overload and the services of that server or network goes down temporarily.Target server and their services are not available till the impact of attack not dissapear.
Victims of DoS attacks often target web servers of high-profile organizations such as banking, commerce, and media companies, or government and trade organizations. Though DoS attacks do not typically result in the theft or loss of significant information or other assets, they can cost the victim a great deal of time and money to handle.
First Dos Attack :-
- first DoS attack was done by 13-year-old David Dennis in 1974. Dennis wrote a program using the “external” or “ext” command that forced some computers at a nearby university research lab to power off.
- The first documented DoS-style attack occurred during the week of February 7, 2000, when “mafiaboy,” a 15-year-old Canadian hacker, orchestrated a series of DoS attacks against several e-commerce sites, including Amazon and eBay. These attacks used computers at multiple locations to overwhelm the vendors’ computers and shut down their World Wide Web (WWW) sites to legitimate commercial traffic.

Introduction to DDoS Attack :-
DDoS attack(distributed denial of service attack) is same as a dos attack, but this is a advance type of denial of services attack which is more powerful then the dos attack. Its clear from the name that there is a some kind of distribution in this attack, and Yes.. there is a distribution of maschines, placed at the different locations to perform the denial of service attack. DDos attack occure when all the machine which are placed at different location are performaing dos attack on the same target and on same time. The main difference is that instead of being attacked from one location, the target is attacked from many locations at once.
The symptoms of a DDoS:-
- Slow access to files, either locally or remotely
- A long-term inability to access a particular website
- Internet disconnection
- Problems accessing all websites
- Excessive amount of spam emails
First DDoS Attack :-
The first DDoS attack occurred way back on July 22, 1999 when a network of 114 computers infected with a malicious script called Trin00 attacked a computer at the University of Minnesota, according to MIT Technology Review. The attack continued for two days and introduced a tactic that has been interrupting business services and websites ever since.

Impact of dos & ddos Attack :-
- The targeted website gose down, which leads to loss in revenue
- When critical network systems are shut down the company’s productivity can grind to a total halt.
- If people are trying to access a website which is crash by a dos attack then it gives a bad impact on the repuation of the company.
- Some more powerful and advance ddos attack leads to the theft of company funds, customer data etc.
- If the attack is powerful ddos attack then some time server are crashed and all data will lose.
DoS & DDoS Attack Technique :-
- SMURF ATTACK :- In this attack large number of icmp packets are broadcast with the intended victim’s spoofed source IP to a computer network using an IP broadcast address.Most devices on a network will by default, respond to this by sending a reply to the source IP address. If the number of machines on the network that receive and respond to these packets is very large, the victim’s computer will be flooded with traffic. This can slow down the victim’s computer to the point where it becomes impossible to work on.
- PING TO DEATH :- In this attack attacker aims to disrupt a targeted machine by sending a packet larger than the maximum allowable size, causing the target machine to freeze or crash.Maximum limit is 65,536 bytes that tcp/ip allow attacker send data packets more than the limit and then Since the sent data packages are larger than what the server can handle, then server can freeze or crash.
- BUFFER OVERFLOW :- In this attacker send lots of data which is more than then the buffer size which cause buffer to overflow and corrupt the data of the buffer. buffer is a temperory storage location in the ram that is used to hold data so that the CPU can manipulate it before writing it back to the disc.
- SYN FLOOD (half-open attack) :- In this attack attacker consume all the available resourse by repeatedly sending initial connection request SYN packet(3 way handshake) attacker are able to take connection to the all available port on the server machine and make it unavailable for the legitimate traffic.

My Dos Attack Tool :-
There are lots of tools available for dos attack and also for ddos attack.Here i am telling you about my python tool which perform dos attack, its very simple and small but working . I made this tool in python which will run on python3.6 or above . I use python modules to make this tool. This tool work only on website which are not using dos/ddos protection.
Python Modules :-
- Thread :- By using this module we make thread
- Argparse :- this module is used to pass the argument to the script like -t for threads -h for help and much more.
- Request :- Request module is use to send traffic.
way of defining :-
python3.8 dos_attack.py -w http://target.website -t 50
Output :-

This tool is available on git hub and the link is :-
Some Big & Famous Attacks :-
- The AWS DDoS Attack in 2020 :- Amazon Web Services, the 800-pound gorilla of everything cloud computing, was hit by a gigantic DDoS attack in February 2020.This was the most extreme recent DDoS attack ever and it targeted an unidentified AWS customer using a technique called Connectionless Lightweight Directory Access Protocol (CLDAP) Reflection. The attack lasted for three days and peaked at an astounding 2.3 terabytes per second.

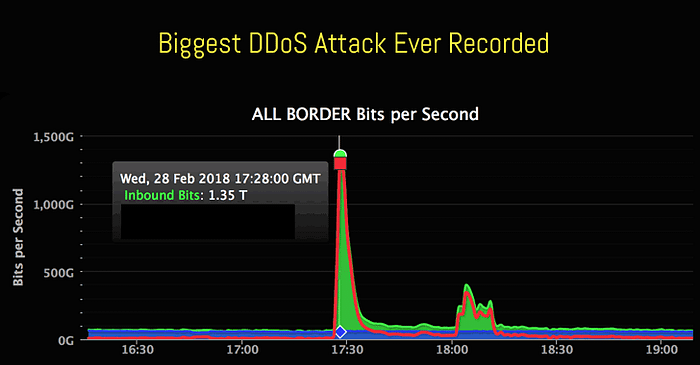
- The February 2018 GitHub DDoS attack :- Prior to this 2.3 Tbps attack, the largest verifiable DDoS attack on record targeted GitHub, a popular online code management service used by millions of developers. This attack reached 1.3 Tbps, sending packets at a rate of 126.9 million per second.
- The Google Attack 2017 :- The attacker used several networks to spoof 167 Mpps (millions of packets per second) to 180,000 exposed CLDAP, DNS, and SMTP servers, which would then send large responses to us. This demonstrates the volumes a well-resourced attacker can achieve. This was four times larger than the record-breaking 623 Gbps attack from the Mirai botnet a year earlier.

- The 2016 Dyn attack :- On October 21, 2016, Dyn, a major Domain Name Service (DNS) provider, was assaulted by a one terabit per second traffic flood that then became the new record for a DDoS attack. There’s some evidence that the DDoS attack may have actually achieved a rate of 1.5 terabits per second.

CONCLUSION :
All type of dos attack are very dangerous which may prove to be very harmful for our systems, networks and machines. So we have to keep in mind to always use Dos security as perior in order to stay away from any dos attack. We are able to defend from dos attack but ddos attack is very powerfull we are not safe from them. According to the prediction of the cisco report ddos attack are growing rapidly, every year millions of ddos attacks are perform.

Expert Opinion :-
Tim Pat Dufficy, managing director of ServerSpace
“The barrier to entry of DDoS attacks in terms of cost has largely gone. That means anyone can launch an attack: organized crime, a group of blackmailers, or just a disgruntled ex-employee or a competitor. And anyone can be the victim.”
References :-
- wikipedia.org
- cloudflare.com
- a10networks.com
Thank You for reading this blog.
If you have any Doubt regarding this then feel free to contact with me
You can follow me on linkedin and twitter
